
|
|
#1 |
|
Участник
|
Rahul Sharma: Dynamics AX 2012 R3 Mobile Apps Configuration Using Self-Signed Certificate
Источник: http://feedproxy.google.com/~r/Rahul...bile-apps.html
============== In the last post we deployed Dynamics AX 2012 R2 DEMO instance on Microsoft Azure. If you don’t have it yet, I will recommend going back to the post “Use Lifecycle Services to deploy Dynamics AX on Azure” and complete the deployment. In this post we are going to setup Dynamics AX Azure instance for Dynamics Mobile Apps using a Self-Signed Certificate. This is only for development / demo environments. In production, we will be using certificate from the Public CA like godaddy etc. Also remember we only have one DEMO VM with all AX components installed on it. As this is going to be a lengthy post, here is the breakdown of the steps we need to follow:
Let's get started. Open Azure management portal to create Service Bus. Remember namespace name as this will used later in the configuration.These steps will be performed on Microsoft Azure Portal Azure Service Bus  Click CREATE and complete the form Click on Connection Information and note down Default Issuer and Default Key, will be used later. Click CREATE and complete the form Click on Connection Information and note down Default Issuer and Default Key, will be used later. Connection InformationAzure VM Setup Connection InformationAzure VM SetupOpen Azure management portal and look for your AX VM.  Dynamics AX VM Dynamics AX VMExample: .cloudapp.net  Azure VM DNS NameAdd an endpoint to the VM Azure VM DNS NameAdd an endpoint to the VMClick on your VM name to modify settings. The next thing you’ll need is an endpoint so that people can actually access it over port 80. You see by default, this VM can only be accessed via PowerShell or RDP which is why there are only two endpoints configured in the management portal.  ENDPOINTS tab and click ADD ENDPOINTS tab and click ADDLets enable HTTPS on port 443 for secure communication. Add a stand-alone endpoint  Click NEXT Click NEXT Select HTTPS and click FINISH You will see endpoint created Select HTTPS and click FINISH You will see endpoint createdChange HOST file on VM Change HOST file name on Azure VM in order to translate machines IP Address into a name (.cloudapp.net) Create Self-Signed SSL Certificate We will use Active Directory Certificate Services to issue a SSL certificate. Make sure this is enabled.  Active Directory Certificate ServicesOn DEMO VM, we will use Contoso Certification Authority that is already installed for us. Active Directory Certificate ServicesOn DEMO VM, we will use Contoso Certification Authority that is already installed for us.Open IIS Manager (inetmgr) to create self-signed certificate request.  IIS - Server Certificates Common name will be same as your Azure DNS Name. IIS - Server Certificates Common name will be same as your Azure DNS Name. Create Certificate Request Create Certificate RequestSave the file. File will look like this and the content of this file will be used for submitting the certificate request. Now open Contoso Certificate Server, https://localhost/CertSrv to complete the certification request.  Certificate Server Certificate Server Request a Certificate Request a Certificate Advance Certificate Request Copy paste the Certificate Request text file content, select Web Server. Advance Certificate Request Copy paste the Certificate Request text file content, select Web Server.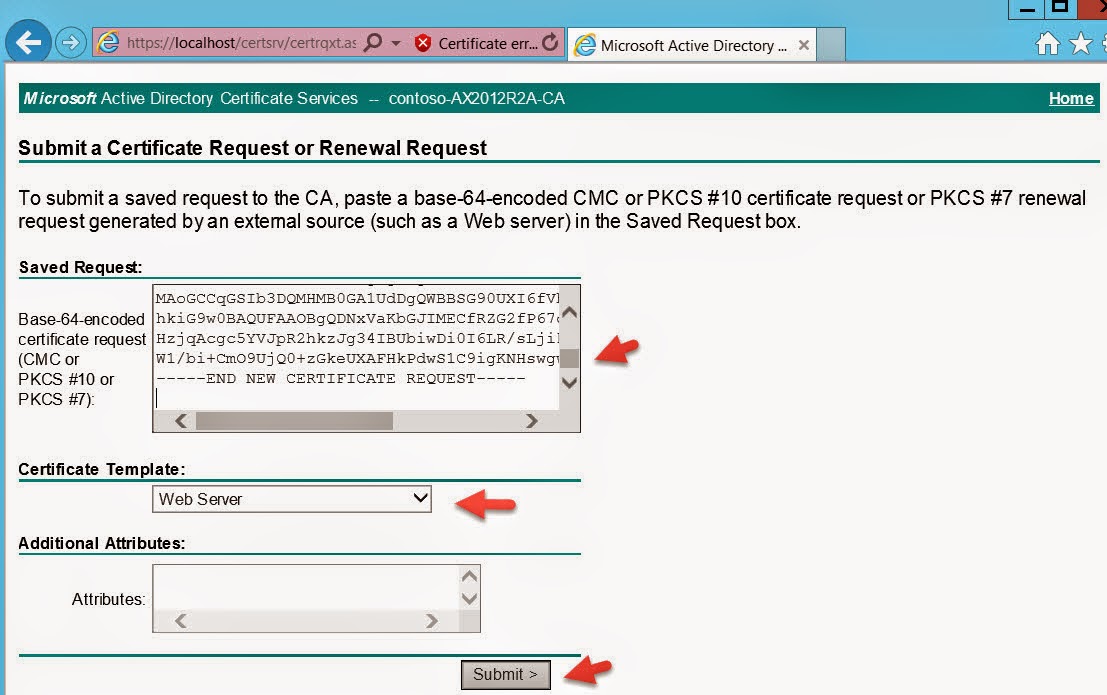 Submit RequestDownload the certificate file. Submit RequestDownload the certificate file.Verify certificate Copy the thumbnail value of the certificate, will be used later while configuring the AX Mobile Connector. Install Self-Signed SSL Certificate We can now install this certificate for both Local Machine and Current User into both Personal and Trusted Root Certification Authorities certificate stores (4 certificate imports). Note: We will be running our Mobile Apps for user contoso\administrator but you can use any user and just install the certificate for that user as well. In production, we will be using the certificate from Public CA. Open the certificate and install. 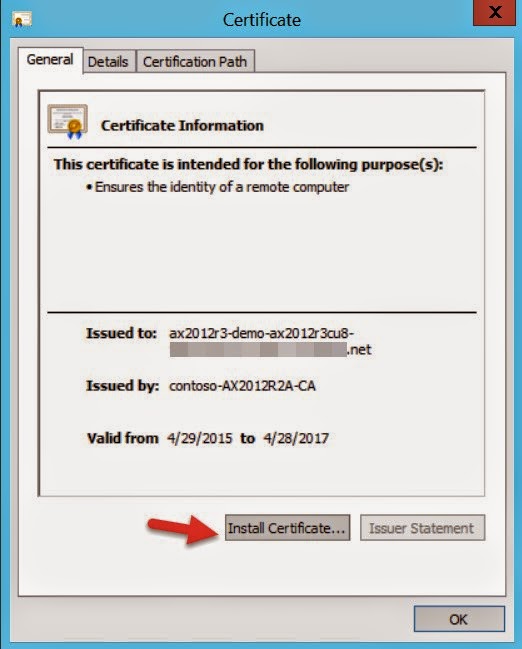 Install Certificate Install Certificate Current User Current User Personal Certificate StoreFinish and import again for Current User and Trusted Root Certification Authorities store. Personal Certificate StoreFinish and import again for Current User and Trusted Root Certification Authorities store.Finish the wizard. Now install the certificate for Local Machine and for both the stores.  Local MachineVerify the import Local MachineVerify the importOpen the console mmc.exe and add two Certificates add-ins. One for current user and one for local computer. You should see the certificate installed on these four locations. Configure IIS - Default Web Site Next step will be to assign our newly created Self-Signed certificate as SSL certificate in IIS for Default Web site. Select HTTPS binding and use the self-signed certificate. Restart IIS (iisreset). Install Active Directory Federation Services (AD FS) There is nothing much here to say, just open Server Manager, click on Add Roles and Features wizard. Select Active Directory Federation Services and complete the wizard. Configure Active Directory Federation Services (AD FS) Once Ad FS is installed, go to the Server Manager, and click on configure federation services on this server. Select the self-signed certificate we created earlier. Federation Service Name should populate your azure dsn name. Note: If you see an error like “contoso\admin could not be dropped, already exist”, simply re-run the federation service configuration wizard and override the database. Once done, you should see these two databases AdfsArtifactStore and AdfsConfiguration.  SQL Server Management StudioGrant access to the users manage private keys SQL Server Management StudioGrant access to the users manage private keysAdd "NT Service\adfssrv" from AX2012R2A. Update Active Directory Federation Services Certificates Open PowerShell and run the following commands
Open AD FS Manager Go to the start menu and search for AD FS Make sure Federation Service name and identifier matches with the public DNS name of the azure VM, .cloudapp.net Right click AD FS and select Edit Federation Service Properties Next we’ll assign our newly created Self-Signed certificate as Service communications certificate, Token-decrypting certificate and Token-signing certificate in ADFS --> Service --> Certificates settings. Select certificates.  Set Server Communication Certificate Set Server Communication Certificate Set Server Communication Certificate Set Server Communication CertificateConfirm Yes on the next screen. Add Token-Signing Certificate Right click on the certificate and set as primary. Select Yes. Add Token-Decryption Certificate Set as Primary. Restart AD FS. Create Relying Party Trust Create a new Relying Party Trust to the Azure Service Bus
These steps will be performed on Microsoft Azure Portal Configure the Azure Service Bus Access Control Services
 Connection Information Connection Information
Open ACS Management Portal
Update Relying Party Trust Open AD FS manager and update Relying Party Trust we created earlier to the Azure Service Bus. Click Update. These steps can be performed on your host laptop/pc Test AD FS You can test ADFS is it is installed correctly and authenticating users. Use this URL to check if users are being authenticated. https://.cloudapp.net/adfs/ls/idpinitiatedsignon.aspx Example: https://ax2012r3-demo-ax2012r3cu8-xx...tedsignon.aspx If you noticed above, we are getting certificate error and that is correct as no one recognizes our VM/Server as trusted public CA. We will fix it in a minute. These steps will be performed on AX DEMO VM Configure Dynamics AX Mobile Connector Open Microsoft Dynamics AX Connector for Mobile Applications.  Before configuring, is in Stopped state. Before configuring, is in Stopped state.Update the following fields
You can also check event viewer for detailed trace. Azure Service Bus Relay will now show listeners. Install, config and run Dynamics AX Mobile Apps Finally, after all this hard work, it’s time to run Dynamics AX Apps :) . For this, we will run Dynamics AX 2012 Expense app on Windows 8.1 machine. Before you can run the app, remember we still need to fix the certification trust error? Lets fix that… Install Self-Signed SSL certificate on your computer/laptop where the app will be running
Windows 8.1 App Login Service connection name is your Azure Service Bus namespace. Successful login and data fetched from AX. Now after that hard work, your Dynamics AX Mobile Apps should work with Azure AX instance. :) Join me on facebook and feel free to post your comments / feedback / queries. Join me on facebook | twitter | linkedin !!! Источник: http://feedproxy.google.com/~r/Rahul...bile-apps.html |
|
|
|
|
| Опции темы | Поиск в этой теме |
| Опции просмотра | |
|